The Problem ZPR Solves
Why networks still fail at security
The Internet was built to connect everything, not to secure it. Firewalls, VPNs, and network security groups attempt to patch the gaps, but overlapping rules and implicit trust leave vulnerabilities. ZPR solves this by embedding authorization and enforcement into the network itself, so every packet is validated before it moves.
Every Packet Verified
Traditional defenses check traffic at boundaries or session start, leaving gaps that attackers can exploit. ZPR validates every single packet as it moves through the network. This continuous verification prevents both accidental leaks and intentional bypasses.
Policy Beyond Perimeters
Firewalls and VPNs enforce policy at a few choke points, creating blind spots elsewhere. ZPR distributes enforcement inside the network itself, so rules apply consistently across datacenters, clouds, and remote access. Security follows the packet instead of depending on a perimeter.
No Implicit Trust
Most systems assume traffic inside the network is safe, but insiders and compromised devices often cause breaches. ZPR requires explicit authorization for every flow, regardless of origin. Nothing is trusted just because it is 'inside.'
ZPR Design Principles
Simple Concepts, Strong Enforcement
ZPR is guided by a small set of principles: every packet must be tied to an identity, policy should be readable and auditable, and enforcement must be distributed rather than centralized. These principles make ZPR both simpler and stronger than traditional approaches.
Identity at the Center
Each user, device, and service has a unique, cryptographically verifiable identity. Policies reference these identities directly, ensuring security decisions reflect real-world entities rather than abstract network addresses.
Attribute-Based Rules
Rules are written against attributes like role, device type, or clearance. This makes these attributes flexible and portable across environments, so the same policies apply consistently whether workloads run on-premises, in the cloud, or across hybrid systems.
Distributed Enforcement
ZPR enforces policy continuously at every node, at line speed. This removes single points of failure, prevents bottlenecks, and ensures that enforcement scales as the network grows.
Performance and Interoperability
Security that fits existing systems
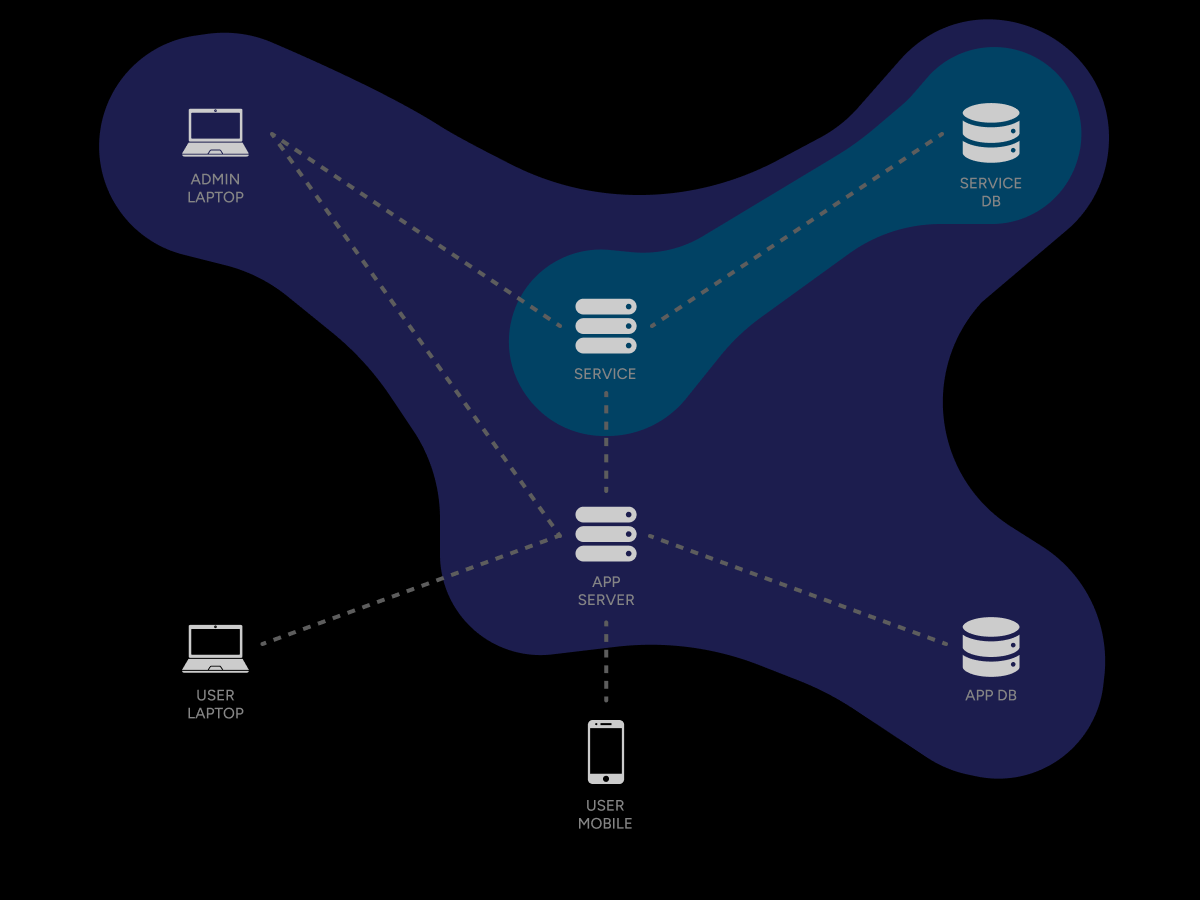
ZPR is designed to integrate with today’s networks. Packet validation is lightweight, applications do not need to be rewritten, and deployments can be done in software or hardware. This makes ZPR secure by design while remaining compatible with existing tools and environments.
Protocol Compatible
ZPR packets carry application data in the same way as IP packets, so applications work without modification. This preserves existing investments while adding security transparently beneath them.
Flexible Deployment
ZPR can run as a software overlay, inside dedicated appliances, or embedded in network cards. This flexibility allows organizations to adopt ZPR incrementally, starting small and expanding as needed.
Fast and Scalable
Visa validation is designed to run efficiently at line speed, even in high-throughput environments. This ensures organizations gain strong security without sacrificing performance or scalability.
