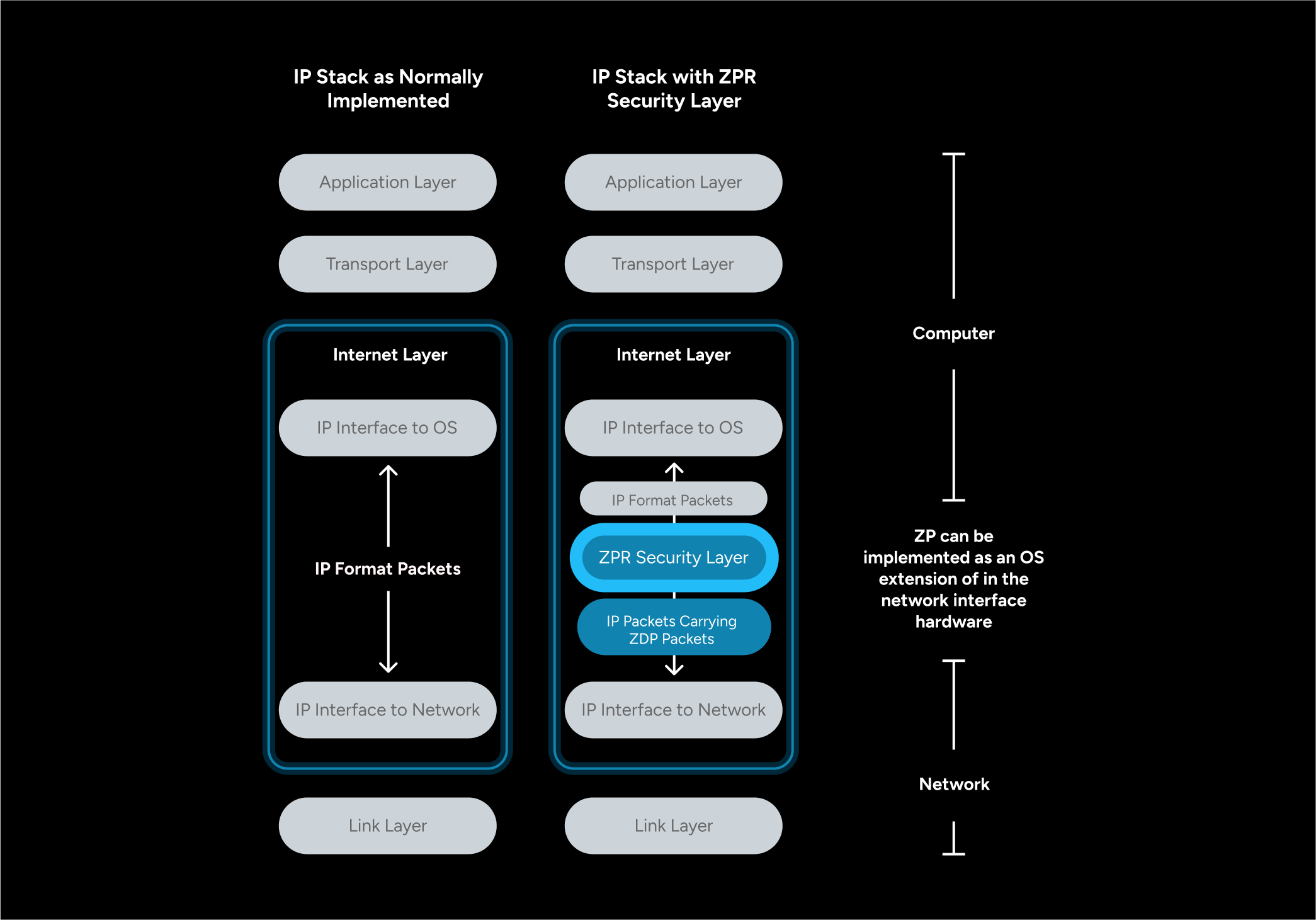
The Internet’s original design left security to the endpoints, creating gaps that firewalls and other patchwork defenses can never fully close. Zero-trust Packet Routing (ZPR) fixes this by embedding policy and identity into the network itself, defining who can connect, under what conditions, and for how long.
Developed by Applied Invention and advanced in collaboration with Oracle, ZPR is part of an open industry initiative to unify network security across datacenters, clouds and distributed environments. It can be implemented in software or hardware, works with existing IP-based applications, and provides organizations with a path to stronger, standards-based security without disruptive infrastructure changes.
ZPR is an open protocol, and the open source reference implementation is in active development. The RFCs, demo code for creating a ZPRnet and the policy language compiler can be found on Github. If you’re interested in knowing more about ZPR as either a potential contributor or an industry partner, more information can be found on our Contact page.